BadBox quickly grows, 190,000 Android gadgets contaminated

Consultants uncovered a botnet of 190,000 Android gadgets contaminated by BadBox bot, primarily Yandex good TVs and Hisense smartphones.
Bitsight researchers uncovered new BADBOX infrastructure, firm’s telemetry reveals that over 192,000 gadgets have been contaminated with the BADBOX bot.
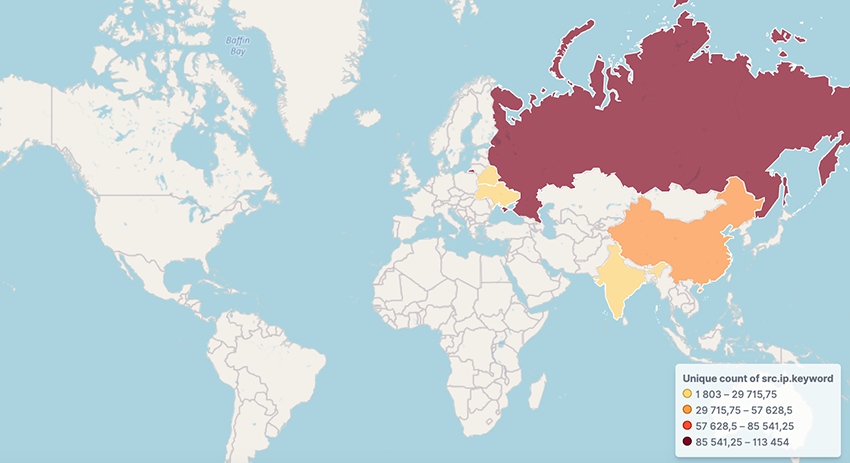
The botnet consists of 160,000 beforehand unseen gadgets, notably Yandex 4K QLED Sensible TVs and T963 Hisense Smartphones. Many of the contaminated gadgets are in Russia, China, India, Belarus, Brazil and Ukraine
Bitsight sinkholed a BADBOX area, logging over 160,000 distinctive IPs in 24 hours, with the quantity tha continues to extend.
BADBOX-infected gadgets ship telemetry to a C2 server upon boot, awaiting directions.
“The coslogdydy[.]in url obtained a number of communications matching that of BADBOX” reads the Bitsight’s report. “This shortly indicated two issues: First, the fashions starting from YNDX-00091 to YNDX-000102 are 4K Sensible TVs from a widely known model, not low-cost Android TV containers. It’s the primary time a significant model Sensible TV is seen instantly speaking at such quantity with a BADBOX command and management (C2) area, broadening the scope of affected gadgets past Android TV containers, tablets, and smartphones.” continues the report “Second, let’s speak quantity. Telemetry collected signifies that greater than 160,000 distinctive IPs talk every day, a quantity that has been steadily rising.”

Lately, The Federal Workplace for Data Safety (BSI) announced it had blocked communication between the 30,000 gadgets contaminated with the BadBox malware and the C2. The gadgets have been all positioned in Germany, they have been all utilizing outdated Android variations.
Technically authorities sinkholed the botnet, an operation that includes redirecting the visitors from contaminated gadgets, which might usually talk with the attacker’s C2 server, to a managed server or “sinkhole” managed by safety researchers or regulation enforcement. Sinkholing isolates the malware and prevents it from executing instructions or stealing knowledge.
The BadBox malware, pre-installed on gadgets, creates electronic mail and messaging accounts for spreading disinformation. The bot conducts advert fraud by accessing web sites within the background and operates as a residential proxy, sharing the person’s web connection for prison actions, which may hyperlink the person’s IP tackle unlawful actions. BadBox also can obtain extra payloads, amplifying the dangers for the customers.
The BSI instructed all web suppliers within the nation with greater than 100,000 subscribers to assist it to hold out sinkholing operations.
In October 2023, cybersecurity researchers at Human Safety discovered a world community of client merchandise, dubbed BADBOX, with firmware backdoors put in and bought via a compromised {hardware} provide chain.
The specialists reported that at the least 74,000 Android-based cell phones, tablets, and Related TV containers worldwide have been shipped with the backdoored firmware.
Merchandise containing the malicious backdoor have been discovered on public college networks all through the USA.
Sadly, the BSI’s latest operation had a restricted impression on BadBox operation, because the regulation enforcement motion was restricted to the nation.
“The BADBOX operation showcases how cyber criminals are additional mastering the artwork of utilizing international provide chains to unfold their malware far and large.” concludes the report. “Whereas this weblog submit centered on contaminated gadgets with greater density in Russia and China, BADBOX malware is an epidemic affecting all international locations and most varieties of android gadgets.”
Observe me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, botnet)







