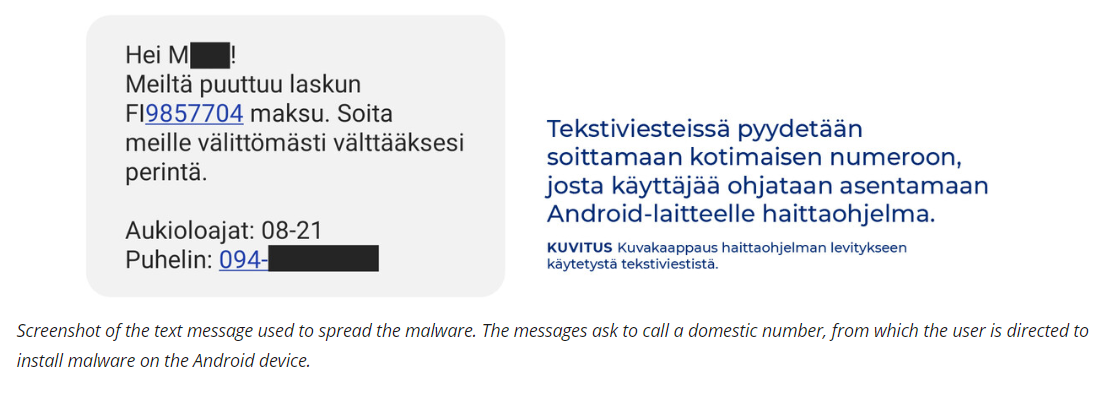
Finland’s Transport and Communications Agency, Traficom, has issued an urgent alert concerning an active Android malware campaign specifically designed to compromise bank accounts. The cybercriminals behind this operation are targeting customers of various banks with sophisticated phishing tactics. Victims report receiving misleading text messages in Finnish, prompting them to contact a seemingly legitimate service number. This number, which impersonates that of a domestic telecom operator or a local network, leads unsuspecting individuals into the trap.
According to Traficom’s detailed warning, these deceitful text messages masquerade as communications from reputable companies, citing reasons such as debt collection or unusual account activities. The ultimate aim is to deceive recipients into believing their financial security is at risk. In a nefarious twist, upon making the call, individuals are duped into downloading what is purported to be antivirus software, specifically a fake McAfee app, to safeguard their device. However, the link provided via a follow-up text message downloads malware instead of any legitimate security software.
This malware, once installed, surreptitiously gains access to the user’s device applications and messages. This includes sensitive online banking details, effectively allowing the perpetrators to siphon off funds from the victim’s bank account. Traficom’s advisory is clear in its caution that the downloaded .apk application, which purports to be a protective measure, is in fact a vehicle for criminal activities.
The agency emphasized that legitimate financial institutions or authorities would never solicit customers to disclose their online banking credentials, conduct transactions, or install unofficial applications through such a method. The advisory continues to highlight that this cyberattack campaign is exclusively targeting Android users, with no current reports of similar fraudulent activities aimed at iPhone users.
In response to the growing threat, the Finnish OP Financial Group has also stepped forward with its own public alert, reinforcing the seriousness of the situation. Both institutions, however, have stopped short of providing detailed insights into the exact malware family involved in these attacks.
As part of the ongoing efforts to mitigate the damage and prevent further victimization, Traficom has recommended several critical actions for those affected. Individuals are urged to immediately contact their banking institutions if they suspect their devices have been compromised, especially if they have conducted financial transactions or entered credit card information. A full reset of the device to factory settings is recommended, with caution to restore from a backup created before the malware’s installation. Furthermore, victims are advised to change passwords for any services accessed via the infected device and to file a police report outlining any financial losses incurred.
Highlighting the importance of vigilance, Google has confirmed that Android’s built-in anti-malware feature, Play Protect, offers automatic protection against known versions of significant threats like Vultur. Ensuring this feature remains active is crucial for ongoing defense against these and other malicious software threats.
As this malware campaign continues to unfold, Traficom and OP Financial Group’s alerts serve as a stark reminder of the sophisticated tactics employed by cybercriminals and the importance of maintaining heightened cybersecurity awareness.
Source






