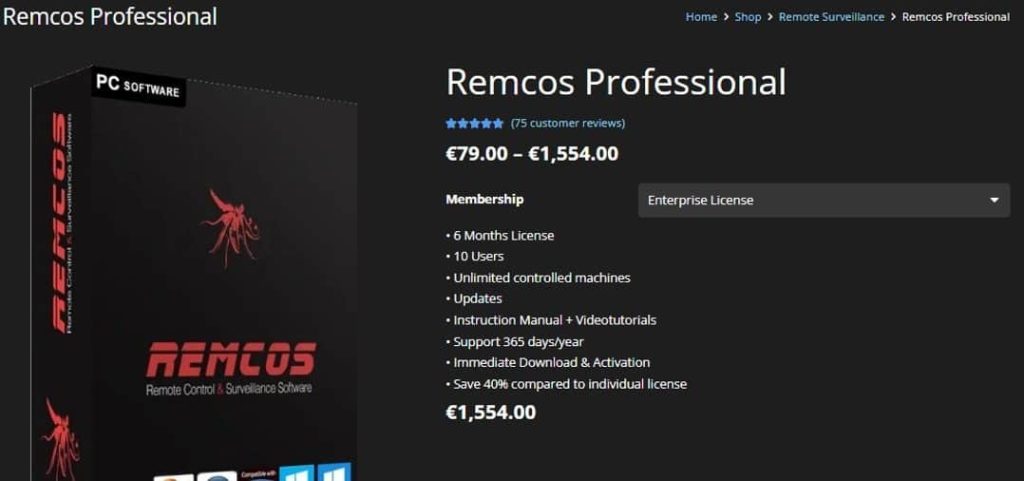
This text explains the inside workings of the Remcos RAT, a harmful malware that makes use of superior strategies to contaminate Home windows methods, steal knowledge, and achieve distant management. Be taught extra about its assault strategies, evasion techniques, and the potential impression on customers.
Cybersecurity researchers at Fortinet’s FortiGuard Labs have uncovered a harmful phishing marketing campaign distributing a brand new Remcos RAT (Remote Access Trojan) variant. This highly effective malware, bought commercially on-line, targets Microsoft Home windows customers and permits risk actors to remotely management contaminated computer systems.
In keeping with Fortinet’s findings, shared with Hackread.com, this marketing campaign was initiated with a misleading phishing e mail disguised as an order notification (OLE Excel doc). Upon opening the connected malicious Excel doc, the CVE-2017-0199 vulnerability is exploited to obtain and execute an HTML Software (HTA) file.
On your data, CVE-2017-0199 is a Distant Code Execution vulnerability that exploits Microsoft Workplace and WordPad’s parsing of specifically crafted information, permitting the MS Excel program to show the content material.
This HTA file, crafted with a number of layers of obfuscation and its code written in numerous scripts, together with JavaScript, VBScript, Base64-encoded, URL-encoded, and PowerShell, delivers the first payload.
It then downloads a malicious executable (dllhost.exe) and executes it through a 32-bit PowerShell course of to extract and deploy the Remcos RAT. The malware modifies the system registry to robotically launch itself upon system startup to make sure persistence.
Remcos connects to a C&C server and sends a registration packet containing system, person, community, and model details about the contaminated system, and receives instructions for data gathering, file operations, distant execution, keylogging, display recording, and webcam seize.
This new variant employs a number of persistence mechanisms, together with superior anti-analysis strategies like Vectored Exception Dealing with. This creates a customized exception handler to intercept/deal with execution exceptions stopping debugging strategies like single-stepping.
Because it doesn’t retailer API names straight, Remcos makes use of hash values to establish APIs, extracting addresses from the Course of Setting Block (PEB) by matching hash values, which makes static evaluation tougher as instruments can’t simply establish the capabilities being known as.
It additionally detects debuggers’ presence by checking debug registers (DR0 to DR7), monitoring API calls generally utilized by debuggers, and utilizing the ZwSetInformationThread() API to cover the present thread from debuggers. Moreover, it makes use of the ZwQueryInformationProcess() API to detect if a debugger is connected to the method and take evasive actions.
Course of hollowing is one other approach it makes use of for evading detection. Researchers discovered that the malware suspends a newly created official course of (Vaccinerende.exe), injects its code into the reminiscence, after which resumes it, making it a persistent risk.
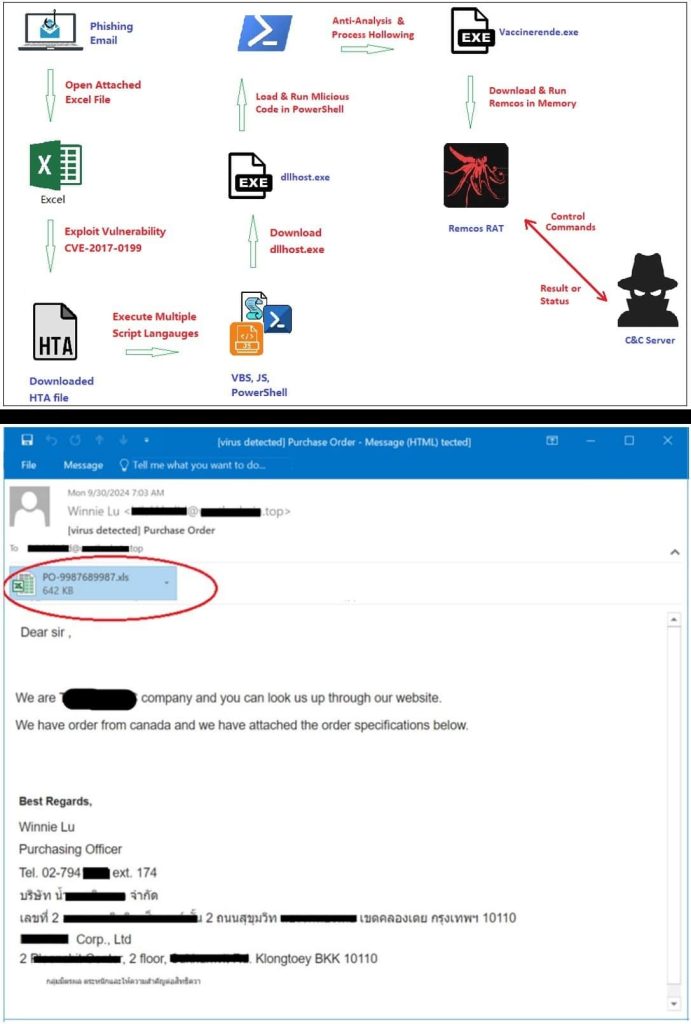
“The malicious code provides a brand new auto-run merchandise to the system registry to keep up persistence and keep management of the sufferer’s system when it’s restarted,” researchers famous of their report.
To guard your self, keep away from clicking on hyperlinks or attachments in emails until they’re official, use security software and antivirus software, preserve software program up to date with the most recent patches, and take into account Content material Disarm and Reconstruction (CDR) service to take away embedded malicious objects from paperwork earlier than opening them.