

A beforehand undocumented Android adware referred to as ‘EagleMsgSpy’ has been found and is believed for use by legislation enforcement companies in China to watch cellular units.
In accordance with a new report by Lookout, the adware was developed by Wuhan Chinasoft Token Data Expertise Co., Ltd. and has been operational since a minimum of 2017.
Lookout presents considerable proof linking EagleMsgSpy to its builders and operators, together with IP addresses tied to C2 servers, domains, direct references in inner documentation, and likewise public contracts.
The researchers additionally discovered clues for the existence of an iOS variant. Nonetheless, they’ve but to achieve entry to a pattern for evaluation.
Highly effective Android adware
Lookout believes that legislation enforcement manually installs the EagleMsgSpy adware after they have bodily entry to unlocked units. This may very well be achieved by confiscating the device throughout arrests, one thing frequent in oppressive international locations.
Lookout has not seen the installer APK on Google Play or any third-party app shops, so the adware is presumably solely distributed by a small circle of operators.
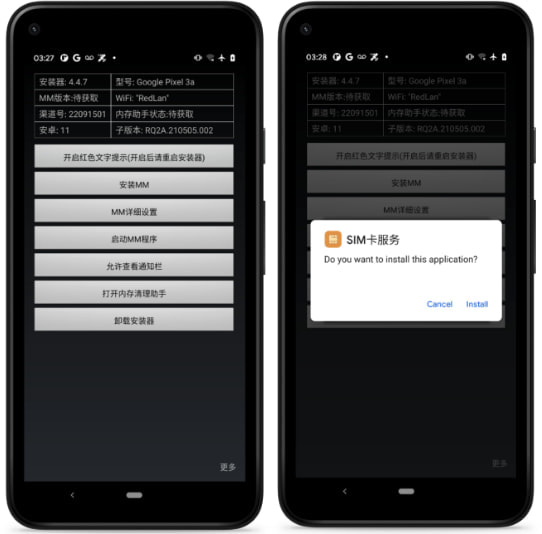
Supply: Lookout
Subsequent variations of the malware sampled by the analysts present code obfuscation and encryption enhancements, indicative of energetic growth.
EagleMsgSpy’s knowledge theft actions embrace focusing on the next:
- Messages from chat apps (QQ, Telegram, WhatsApp, and many others.)
- Display screen recording, screenshots, and audio recordings.
- Name logs, contacts, SMS messages.
- Location (GPS), community exercise, put in apps.
- Browser bookmarks, exterior storage information.
Information is saved briefly in a hidden listing, encrypted, compressed, and exfiltrated to the command-and-control (C2) servers.
The malware options an administrator panel referred to as “Stability Upkeep Judgment System.”
The panel permits distant operators to provoke real-time actions like triggering audio recordings or displaying the goal’s contacts’ geographical distribution and communication alternate.
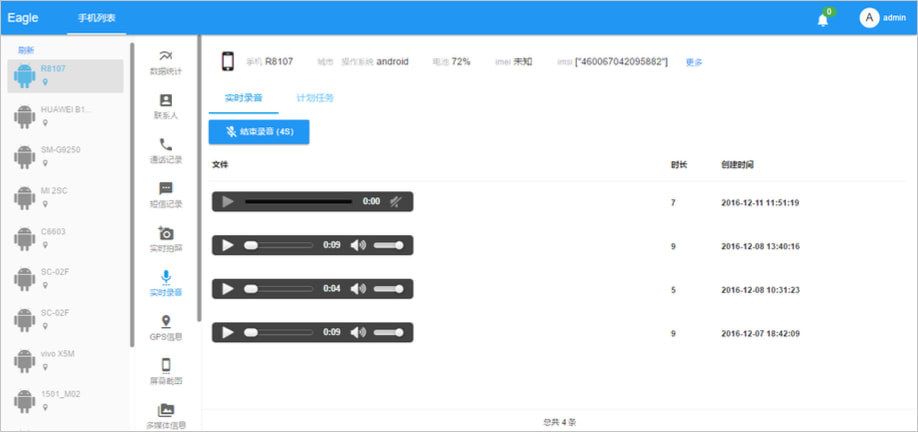
Supply: Lookout
Behind EagleMsgSpy
Lookout says with excessive confidence that the creators of EagleMsgSpy is Wuhan Chinasoft Token Data Expertise, tied to the malware via overlaps in infrastructure, inner documentation, and OSINT investigations.
For instance, a website the corporate makes use of for promotional supplies (‘tzsafe[.]com’) additionally seems in EagleMsgSpy’s encryption strings, whereas the malware’s documentation immediately references the agency’s identify.
Moreover, check system screenshots from the admin panel correspond to the placement of the agency’s registered workplace in Wuhan.
Relating to the adware operators, Lookout claims that C2 servers are tied to domains of public safety bureaus, together with the Yantai Public Safety Bureau and its Zhifu Department.
Historic IP data additionally present overlaps with domains utilized by bureaus in Dengfeng and Guiyang.
Lastly, the identify of the admin panel means that it is systematically utilized by legislation enforcement or different authorities companies.






