
[Updated] November 8, 2024: “CISA Provides Android Vulnerability CVE-2024-43093 to KEV Catalog”
Google lately rolled out the November 2024 Android safety replace, resolving 40 safety vulnerabilities. Amongst these, two zero-day flaws (CVE-2024-43093 and CVE-2024-43047) stand out resulting from lively exploitation within the wild, sparking issues about potential focused assaults.
These vulnerabilities influence key components of the Android system, together with the framework and Qualcomm chipsets, making well timed patching vital for customers to defend their units towards compromise.
Lively Privilege Escalation Risk in Android Framework (CVE-2024-43093)
The primary vulnerability beneath lively exploitation in Google’s November 2024 Android replace, CVE-2024-43093, is a privilege escalation flaw inside the Android Framework.
This safety flaw permits unauthorized entry to delicate directories, comparable to “Android/information,”“Android/obb,” and “Android/sandbox,” together with their respective subdirectories. By leveraging this vulnerability, attackers can acquire elevated privileges, doubtlessly enabling them to carry out unauthorized actions or entry delicate information.
Affecting Android variations 12, 13, 14, and 15, this flaw impacts a variety of units throughout the Android ecosystem. Though particular strategies of real-world exploitation are usually not disclosed, Google has confirmed proof of restricted, focused exploitation. This highlights the important want for system house owners to use the newest safety replace to guard towards potential assaults.
CISA Provides Android Vulnerability CVE-2024-43093 to KEV Catalog
CISA has issued an alert asserting the addition of CVE-2024-43093 Android Framework Privilege Escalation Vulnerability to its Identified Exploited Vulnerabilities (KEV) Catalog. This vulnerability may allow unauthorized privilege escalation, permitting attackers to entry delicate Android directories with out person consent. Federal companies should apply the mandatory patch by November 28, 2024 to forestall exploits and stay compliant.
Excessive-Severity Zero-Day Vulnerability in Qualcomm DSP Service (CVE-2024-43047)
CVE-2024-43047 (CVSS 7.8) is a critical Use-After-Free vulnerability impacting Qualcomm’s Digital Sign Processor (DSP) service. This flaw, if exploited, may result in reminiscence corruption, permitting attackers to escalate privileges and compromise affected units.
Given the in depth use of Qualcomm chipsets throughout Android units, the vulnerability poses a big safety danger for a broad vary of units.
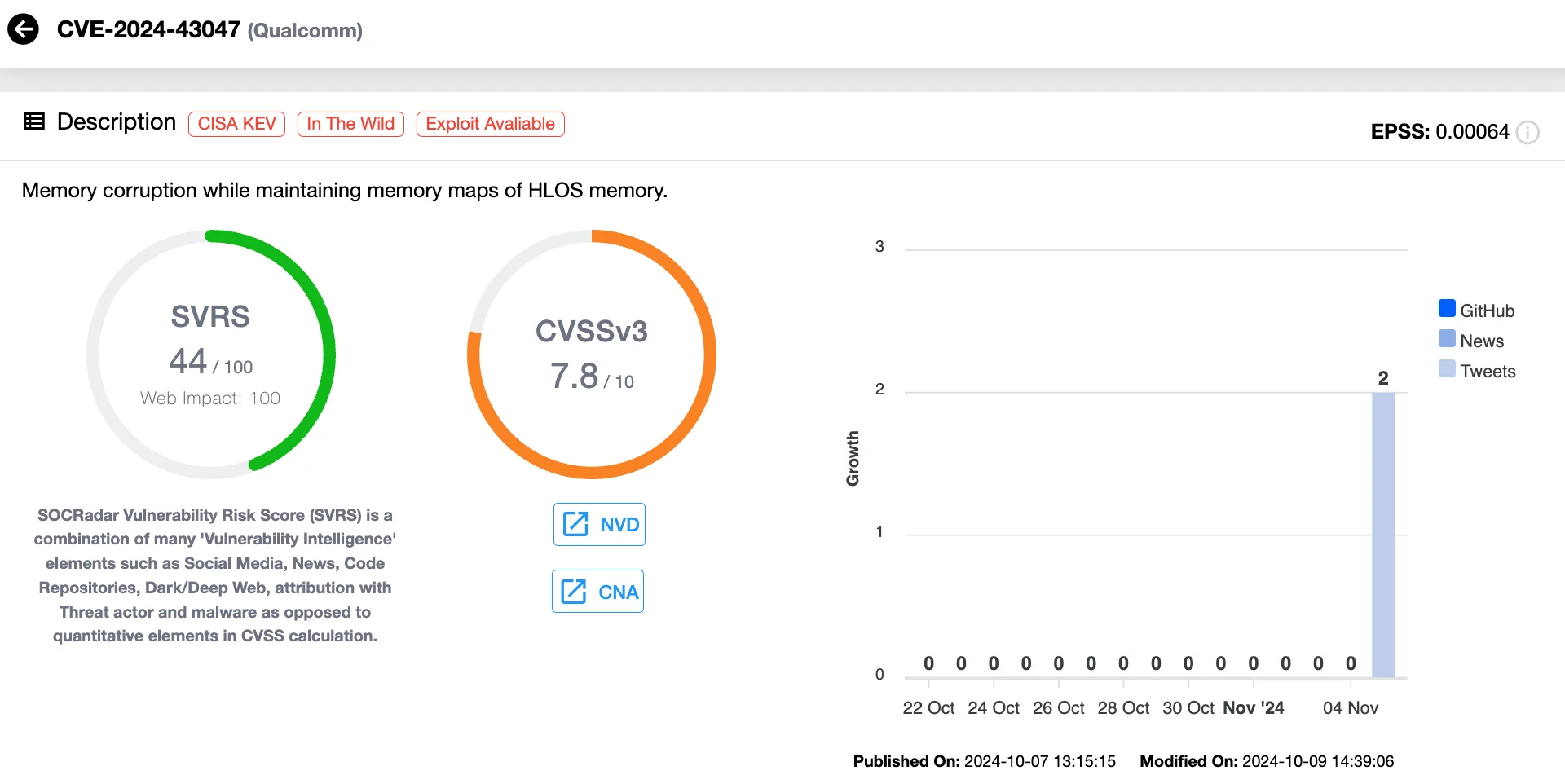
Vulnerability card of CVE-2024-43047 (SOCRadar Vulnerability Intelligence)
This vulnerability was initially reported by researchers from Google Undertaking Zero, and its lively exploitation was documented by Amnesty Worldwide’s Safety Lab. Whereas Qualcomm launched a patch for this flaw in October, Google’s inclusion of CVE-2024-43047 within the November safety replace ensures that it reaches a variety of Android units, serving to customers shield their units with this important repair.
Google’s advisory additionally highlights attainable focused exploitation of CVE-2024-43047, although particulars of the exercise are presently not reported.
We lined CVE-2024-43047 and extra vulnerabilities addressed in Qualcomm’s October 2024 Safety Bulletin in a earlier weblog put up, which you’ll learn here.
Keep Protected with SOCRadar’s Actual-Time Vulnerability Intelligence
To guard towards safety threats like CVE-2024-43093 and CVE-2024-43047, staying knowledgeable about new vulnerabilities and lively exploits is important. As Android devices more and more function key instruments for enterprise and private use, addressing flaws rapidly can stop important safety incidents. Whereas Google’s common updates assist mitigate dangers, organizations profit from an added layer of proactive menace intelligence to maintain tempo with evolving threats.
SOCRadar’s Vulnerability Intelligence, supplied beneath the Cyber Threat Intelligence module, is designed to help this want by providing real-time monitoring of high-risk vulnerabilities, together with these with lively exploitation traits.
SOCRadar’s Vulnerability Intelligence
With well timed alerts, complete vulnerability particulars, and actionable insights, this device permits your group to prioritize important patches and reinforce its safety posture, safeguarding your assets earlier than vulnerabilities are extensively exploited.
Safe Your Machine with November 2024 Android Safety Updates
The November 2024 Android safety replace is split into two patch ranges to deal with a broad spectrum of vulnerabilities.
The November 1 patch stage targets core Android parts, together with the framework and system, making certain foundational protections. The November 5 patch stage particularly addresses vulnerabilities in {hardware} parts supplied by distributors like Qualcomm, MediaTek, and Creativeness Applied sciences, amongst others.
Given the lively exploitation of important vulnerabilities like CVE-2024-43093 and CVE-2024-43047, it’s important for customers to put in this replace promptly. Delaying patches leaves units uncovered to safety dangers, particularly as menace actors are already exploiting these flaws in focused assaults.
For added particulars on these updates and additional advisories, confer with the Android Security Bulletin for November 2024.








