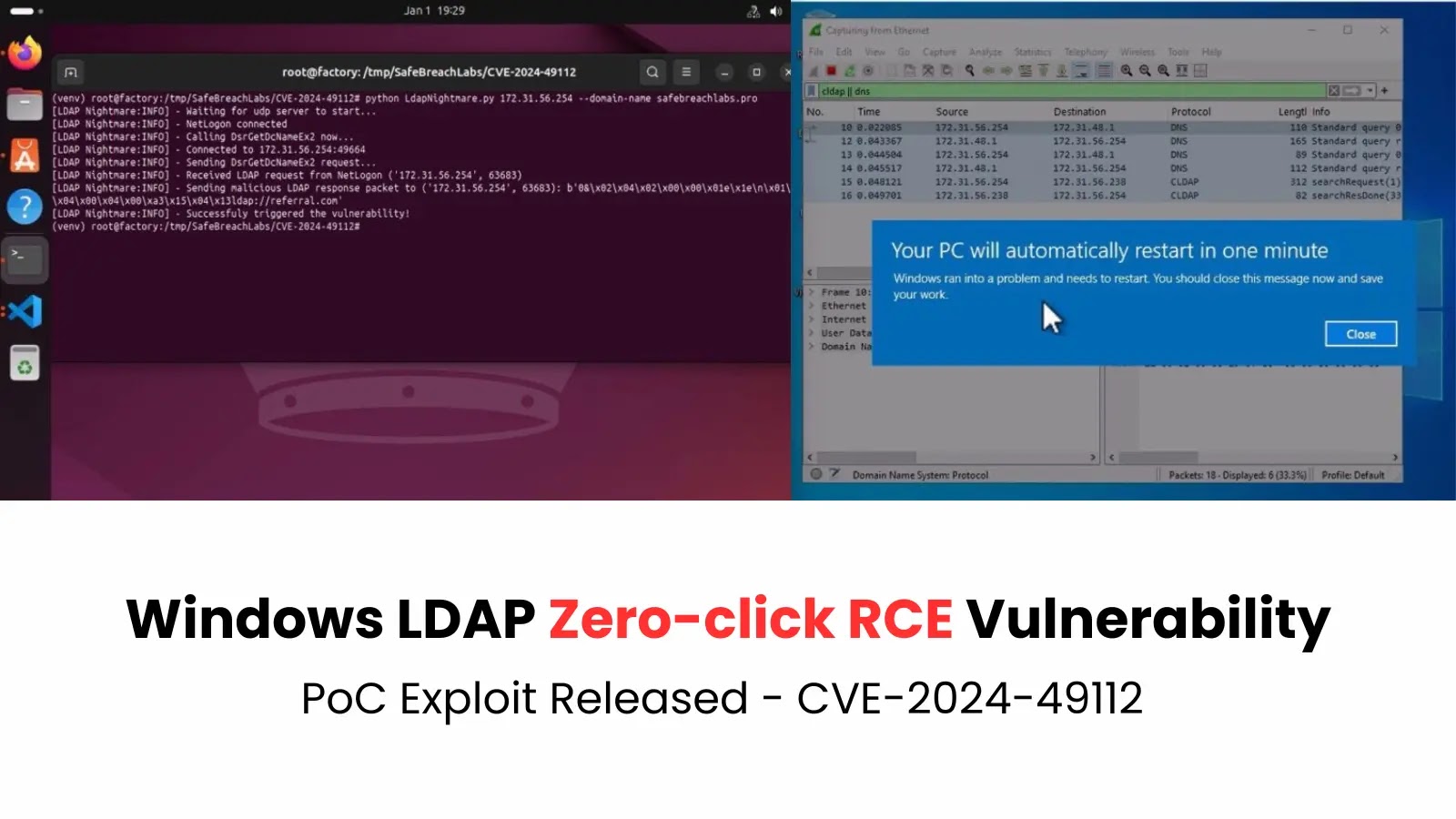
Researchers unveiled a proof-of-concept (PoC) exploit for a important vulnerability in Home windows Light-weight Listing Entry Protocol (LDAP), tracked as CVE-2024-49112.
The flaw, disclosed by Microsoft on December 10, 2024, throughout its Patch Tuesday replace, carries a CVSS severity rating of 9.8 and poses a major danger to enterprise networks.
CVE-2024-49112 is a distant code execution (RCE) vulnerability that impacts Home windows servers, together with Area Controllers (DCs). DCs are important elements in organizational networks as they handle authentication and consumer privileges.
Exploiting this flaw may enable attackers to crash unpatched servers or execute arbitrary code inside the context of the LDAP service, probably compromising complete domains.

The vulnerability stems from an integer overflow in LDAP-related code. An unauthenticated attacker can exploit it by sending specifically crafted RPC calls to set off malicious LDAP queries. If profitable, this might result in server crashes or additional exploitation for RCE.
PoC Launched for CVE-2024-49112
SafeBreach Labs developed a zero-click PoC exploit, dubbed “LDAPNightmare,” demonstrating the criticality of CVE-2024-49112. The exploit crashes unpatched Home windows servers by leveraging the next assault move:
- An attacker sends a DCE/RPC request to the sufferer server.
- The sufferer queries the attacker’s DNS server for info.
- The attacker responds with a hostname and LDAP port.
- The sufferer sends an NBNS broadcast to find the attacker’s hostname.
- The attacker replies with its IP handle.
- The sufferer turns into an LDAP consumer and sends a CLDAP request to the attacker’s machine.
- The attacker sends a malicious referral response, inflicting LSASS (Native Safety Authority Subsystem Service) to crash and reboot the server.

SafeBreach verified that Microsoft’s patch successfully mitigates this vulnerability by addressing the integer overflow subject.
The vulnerability impacts all variations of Home windows Server previous to patching, together with Windows Server 2019 and 2022. Exploitation may allow attackers to take management of area environments, making them a primary goal for ransomware gangs and different menace actors.
Organizations are urged to:
- Apply Microsoft’s December 2024 patch instantly.
- Monitor for suspicious DNS SRV queries, CLDAP referral responses, and DsrGetDcNameEx2 calls till patching is full.
- Take a look at their environments utilizing SafeBreach’s PoC device, which is out there on GitHub.
The discharge of this PoC highlights the urgency of addressing CVE-2024-49112. Whereas SafeBreach’s analysis underscores the vulnerability’s potential influence, it additionally offers organizations with instruments to confirm their defenses.
Microsoft has already released patches for the vulnerability; Enterprises should prioritize patching and implement strong monitoring to safeguard important infrastructure in opposition to exploitation.
Examine Actual-World Malicious Hyperlinks, Malware & Phishing Assaults With ANY.RUN – Try for Free







