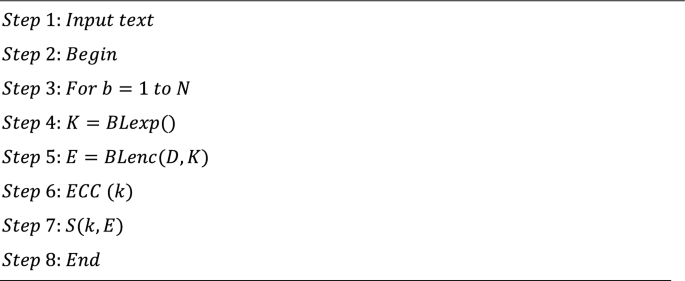A radical rationalization of the urged design is described on this part. Primarily, the enter APK information/ information are preprocessed to extract options. The collection of optimum options is supported out by way of the Squirrel search optimization (SSO) course of. After that, the DL-based model-Adaptive deep saliency AlexNet classifier is offered to detect and classify information as malicious or regular ones. The detected information which aren’t malicious are saved in a cloud server. For secured storage of knowledge within the cloud, the hybrid cryptographic mannequin (Hybrid Homomorphic ECC & Blowfish) is employed which incorporates key computation and key era course of. The cryptographic scheme consists of encryption and decryption of knowledge after which the app response is discovered to realize a decrypted consequence upon person request. The illustration of the entire manuscript workingflow is proven in Fig. 1.
Experimental setup
The analysis setup of the proposed system is expressed right here by taking the web accessible dataset as https://github.com/harrypro02/Android-Malware-Permission-Based-Dataset’, and maldroid-2020, which can consist of various permissions for Android malware identification on cell units with completely different parameters comparable to storage, picture, opcode, system name, and all permissions contained in the cell machine. Then the preprocessing is dealt with with the mannequin to coach the DL mannequin from the accessible dataset. To get the specified consequence, the dataset might encompass 15,000 entries in 5 rows and 1204 columns with malware information, and the traditional dataset is preprocessed into the coaching mannequin. After coaching, characteristic extraction is finished with the SSO optimization algorithm to enhance mannequin efficiency with an environment friendly studying charge of 0.01 and L2 regularization to beat the loss after characteristic extraction. Cryptographic key administration is processed with homomorphic ECC and Blowfish encryption to make sure safety is maintained all through the method of decrypting the affected information processed by the ransomware. After encryption, mannequin efficiency is analyzed with 50 epochs of coaching and 80/20 testing utilizing adaptive deep saliency. AlexNet is configured with a dense layer and an Adam optimizer with a Relu activation perform to seize Android malware with excessive accuracy in contrast with different conventional deep studying fashions accessible. Lastly, this mannequin ensures the mixed deep studying and cryptographic strategies work very effectively in detecting Android malware with excessive accuracy, and the scientific design of the proposed mannequin is expressed within the under sections.
Enter information cleansing
At first, the enter information (software to be put in) is taken and preprocessed to take away redundant and pointless information. The preprocessing on this mannequin goals to guage the aptitude to guard towards the embedded ransomware code in Android apps. To realize this, a particular key for preprocessing the bytecodes from Android apps is used and exploited as a construction. A hybrid cryptography mannequin was employed to find out vital options for the discovering of Android malware. Earlier than using the detection algorithm, preprocessing is carried out for a dataset index format. This strategy takes care of changing the method of dex information to an acceptable APK format. This in flip consists of dex-file compiling as a setup that adapts to APK. For sustaining the designing compatibility of cell units, modules from JVM of Omni Rom (OR) to this transformation are employed. After the completion of the conversion course of, the mannequin analyses the textual content phase of each APK file to extract opcode directions. This mannequin consists of mannequin creation for detecting ransomware and for securing cloud server information which follows all the crypto-code. The APK picture was taken for every software and thus extracts the respective bytecode from the phase of .apk. the mannequin calculates the info prevalence and thereby sends them to the method of characteristic extraction.
Characteristic extraction & SSO (squirrel search optimization) optimization-based choice
The classification of malware relying on grey-scale picture extraction is a brand new strategy. This has proved to be an efficient software for static evaluation. It’s the picture that’s expressed in gray colour. In accordance with the logarithmic relationship, the brightness from white to black colour is thus divided into 256 grades. Varied bodily information from graphs may trigger a respective distinction in greyscale, and textures which confirms the reflection within the visible discipline. For exploiting the malware texture distinction, an interactive disassembler was employed first (IDA) for attaining binary information into smaller models every one in every of them includes of eight bits and is thus transformed to unsigned integer format in a variety 0–255. In a grey-scale picture, 0 and 255 signify white and black correspondingly. Finally, the file reworked is thus mapped to a matrix termed ‘gray scale matrix’. The matrix width is often initialized to 2n. On this mannequin, n is the same as 8. Furthermore, the matrix is adopted to characteristic expression. In order to undertake this, the grey-scale matrix is thus mapped as a one-dimensional vector termed ‘gray scale vector’.
The options extracted are then subjected to an optimum collection of options in order to pick out optimum ones. The algorithm of SSO updates the place of the people as per the current season, the form of people, and the predator’s look.
Initialization of inhabitants: Assume (mathcal{N}) because the variety of people, and ({SS}_{U}) and ({SS}_{L}) are the bounds of exploration area. As per the system, the people are produced randomly in Eq. (1):
$$SS_{I} = SS_{L} + {mathcal{R}}left( {1,D} proper) occasions left( {SS_{U} – SS_{L} } proper)$$
(1)
({SS}_{I}) signifies ith particular (left(i=1,dots ,mathcal{N}proper)), (mathcal{R}) signifies the random quantity amongst 0 to 1 & D denotes the issue dimension.
Inhabitants classification
On taking the minimization difficulty into consideration, SSO wants one squirrel at each tree, whereas assuming the overall variety of squirrels are (mathcal{N}). The inhabitants’s health perform is thereby ranked in an ascending order. The squirrels are segregated into 3 sorts: Squirrels positioned at hickory timber ({S}_{H}), squirrels at acorn timber ({S}_{A}) and squirrels at regular timber ({S}_{N}). To seek out the best meals trigger, the terminus of ({S}_{A}) is ({S}_{H}) and terminus of ({S}_{N}) is decided randomly as whichever ({S}_{H}) or ({S}_{A}).
Place updation
The squirrel’s place is thus up to date in Eqs. (2 and 3).
$$left{ {start{array}{*{20}l} {SS_{I}^{t + 1} = SS_{I}^{t} + {mathcal{G}} occasions {mathcal{C}} occasions left( {SS_{H}^{t} – SS_{I}^{t} } proper)} hfill & {if;{mathcal{R}} > {mathcal{P}}_{AP} } hfill {random;location} hfill & {In any other case} hfill finish{array} } proper.$$
(2)
$$left{ {start{array}{*{20}l} {SS_{I}^{t + 1} = SS_{I}^{t} + {mathcal{G}} occasions {mathcal{C}} occasions left( {S_{AI}^{t} – SS_{I}^{t} } proper) } hfill & {if;{mathcal{R}} > {mathcal{P}}_{AP} } hfill {random;location} hfill & {In any other case} hfill finish{array} } proper.$$
(3)
({mathcal{R}}) designates a random quantity & ‘t’ signifies the present iteration. ({mathcal{P}}_{AP}) denotes the likelihood of hunter arrival whose charge is 0.1. If (mathcal{R}>{mathcal{P}}_{AP}), then there shall be predator absence & the squirrel slides into the forest for meals. (mathcal{R}le {mathcal{P}}_{AP}), the hunters would possibly seem & squirrels need to lower the actions of meals forage since they’re in danger. At the moment, the squirrel’s positions are randomly relocated. ({mathcal{C}}) specifies the fixed of worth 1.9 & (mathcal{G}) signifies gliding distance. ({S}_{AI}^{t}) denotes randomly chosen particular person squirrels from ({S}_{A}.) Gliding distance is taken into account as in Eq. (4)
$${mathcal{G}} = frac{{{mathcal{G}}_{H} }}{{tan left( theta proper) occasions {mathcal{S}}}}$$
(4)
({mathcal{G}}_{H}) denotes the persistent whose worth is 8 & (mathcal{S}) is the relentless of worth 18. (tanleft(theta proper)) signifies the crusing angle. As soon as the variety of iterations exceeds the intense quantity of iterations, the person’s motion is stopped. Or else, the above steps get repeated.
Adaptive deep saliency AlexNet classifier
As soon as the collection of options is made, the mechanism of classification is employed in order to acknowledge the assaults. On this effort, the group strategy is the ultimate stage of the detection mechanism. The detection must be made earlier than the safety mechanism. For the classification course of, adaptive deep saliency AlexNet classifier is employed to categorise the info as malignancy or benignity labels. The dataset is subdivided into 2 phases for estimating the areas to check and prepare. This section covers dataset vector coaching with its respective lessons, whereas the output identifies whether or not the enter picture is gentle or deadly. This classifier mannequin is skilled and examined with the kernel perform of RBF to realize a greater end result.
The urged Adaptive deep saliency AlexNet classifier mannequin detects whether or not the info is malicious or not. The information within the phrases earlier than step t of CNN structure is simply too employed because the enter on the time of phrase processing of step t. The early cell information are gathered from cells and phrases are thus given as inputs. The little references sense the repeated picture over one cell. The cell sequence of structure is one other reference. The quantity of textual content offered in every instance of knowledge doesn’t develop into a particular worth of pure language processing points. For executing every textual content, the scale of the preparations have been diminished to worth. As soon as the worth of the association is lower than the specified worth, the sequence is thus stuffed as a worth. As soon as the sequence dimension exceeds the talked about worth, the remaining are rejected.
The AlexNet CNN mannequin includes 5 layers of convolution, two totally related layers which are related fully, and one recurrent layer. The layers of CNN have been employed for studying middle-level patterns of visible much like the primary 5 fashionable layers of AlexNet seven layer. The layer of RNN is employed for studying the dependency of area amongst visible patterns of the center layer. In each ultimate, layers, 2 totally related RNN outputs have been gathered and the illustration of a worldwide picture was realized. The classification of the SoftMax layer must be utilized subsequently to N-way (N signifies the category quantity).
As soon as the info is classed as assault or regular, then the traditional information is saved in a cloud server. From the cloud server, the info must be encrypted with a key in order to allow secured technique of cloud storage. For the secured storing within the cloud, the computation of key or key era is carried out adopted by a hybrid cryptographic strategy to allow encryption and decryption course of. That is defined in subsequent sections.
Computation of key utilizing Okay-Facilities Diffie-Hellman (KC-DH)
For the secured technique of storage in cloud, the info must be encrypted and guarded with key. For key computation, the strategy of Okay-centers Diffe-Hellman (KC-DH) is employed at which the era of key’s carried to share non-public key with which they may change information over insecure channel. Nevertheless, the non-public key shouldn’t be distinctive which generates each information sharing transaction at non-public key have to be random. The algorithm for this key computation strategy is proven under:
That is the discrete logarithm difficulty, which is infeasible computationally for bigger p. The computation of discrete quantity logarithm modulo p takes an identical quantity roughly the identical time of quantity since factoring the 2 prime merchandise as related as p, which is what the RSA cryptosystem safety lies on. Subsequently, this protocol ECC-DH is secured roughly as RSA.
Hybrid cryptography utilizing Homomorphic ECC & Blowfish strategy
The hybrid homomorphic ECC and blowfish-dependent cryptographic scheme was urged on this mannequin which the multilevel encryption to alternate information between server and consumer in a mannequin of public SaaS. It’s primordial to protect confidentiality earlier than outsourcing or sending info in each instructions from the consumer to the cloud & vice versa. Consequently, unauthorized entry by non-allowed customers could be secured to ban safety constraint threats which are coming from intruders. This hybrid mannequin is obtainable during which the cloud server information uploaded is subsequently encrypted utilizing a blowfish technique to reinforce the facet of safety thus preserving information privateness. But, for prime safety, keys used within the encryption course of are dealt with subsequently and encrypted by the ECC strategy. This hybrid mannequin not solely ensures integrity & confidentiality but additionally gives authenticity. The urged mannequin makes use of two sorts of cryptography approaches that are a symmetric strategy (blowfish) and an uneven algorithm (ECC). Subsequently, this mannequin of hybrid mannequin integrates two approaches to learn the encryption course of. The blowfish strategy or symmetric mannequin is thus employed to encrypt information that’s saved within the cloud. Thus, the decryption course of is a reverse one carried out in information outsourcing. The uneven mannequin is ECC & thus employed within the administration & encryption of encrypting keys. The integrity of homomorphic ECC and Blowfish scheme processes enhances safety in cell environments the place ECC processes have robust safety with small key sizes in comparison with conventional fashions comparable to RSA. The 128-bit key of ECC gives the identical safety stage because the 1024-bit key of RSA. Equally, Blowfish is acquainted for its velocity and effectivity in a small, much less resource-constrained atmosphere like Android with 64-bit blocks for information encryption. Combining these two schemes improves confidentiality and is efficacious for cell environments with out exposing all information contained in the service supplier. With this feature, hybrid cryptography is extra environment friendly than utilizing AES and different conventional strategies. The proposed homomorphic ECC and Blowfish scheme has the power to carry out computation by bettering safety enhancement, the place the data contained in the cell information stays protected even throughout processing in contrast with conventional safety schemes.
The strategy goals to guard information which are exchanged between server and consumer in SaaS. Therefore, the method of encryption is thereby carried out at information which is to be up to date by the consumer beforehand that is transferred to a server. The reverse course of is employed on a consumer earlier than that is despatched to the server. The reversing course of is employed on downloading information, subsequently consumer decrypts information downloaded from server that are from server that would be capable of employed. Therefore, the functioning of the system is thus talked about under.
Knowledge importing
Knowledge is encrypted from plain to cipher textual content earlier than importing by way of the blowfish strategy. After that, encryption keys are thus encrypted by the ECC algorithm. Lastly, each encrypted information & generated secret keys have been despatched to a cloud server within the type of cipher textual content.
Knowledge downloading
The reverse course of was carried out on downloading information. At first, an encryption key’s thus decrypted utilizing the ECC strategy. Then, the generated key’s employed to decrypt information utilizing the blowfish strategy. Thereby plain textual content is successfully recovered. On this manner, unauthorized customers couldn’t make use of information as it’s in a safe method, therefore they aren’t competent to entry them with out utilizing decryption. The multilayer encryption makes use of blowfish because the preliminary layer & ECC within the subsequent layer which is blowfish on enter textual content after which the encryption end result attained is delivered to the subsequent layer at which the encrypted blowfish keys are encrypted via ECC. The ultimate encryption output is achieved. For the understanding objective, just a few variables &v some features listing is given by (Fb, E(b,ok), P(F), Ek,) & (Pk) that are employed within the urged strategy as given under:
Alone the encryption algorithm provided as a decryption strategy is nothing however the reverse technique of that is as follows:
On this, (D) is the enter information file, the encrypted file is E, and N signifies the variety of blocks in (D), (E(b,ok)) signifies the encryption perform that encodes (textual content blocks(b)) laterally with (ok key) utilizing projected (IABE-PPKGC) system. The P(F) perform would possibly enable (Fe) encrypted information to be despatched them in a cloud server. The (Ek) perform subsequently encodes blowfish key with using (ECC) system. (Pk) signifies the perform that allows encrypted key ((K1)) that are produced by way of (Ek) in a cloud server.
The mathematical equation of the proposed Hybrid Cryptography is talked about under, Elliptic curve cryptography has key era, key alternate, and symmetric key derivation as follows.
-
(i)
Non-public key-PK, Public Key-PuK, the place non-public key choose integer within the vary of (1, n-1) the place n is the order in base level ECP-Elliptic Curve Level, then PuK is computed in Eq. (5)
-
(ii)
Now key alternate is processed with a shared secret key as SK, then SK is computed in Eq. (6)
$$SK=P{Okay}_{1}Pu{Okay}_{2}=P{Okay}_{1}left(P{Okay}_{2}ECPright)=P{Okay}_{2}left(P{Okay}_{1}ECPright)=P{Okay}_{2}Pu{Okay}_{1}$$
(6)
-
(iii)
Now the symmetric key derivation is derived utilizing secret key SK and Symmetric Key as SyK utilizing a Key creation Perform as KCF expressed in Eq. (7)
-
(iv)
Blowfish has divided into two elements to make smaller keys for each encryption and decryption to resolve computational overhead the place P is for Plaintext and C for Ciphertext. The encryption and decryption course of began with block dimension as b and that i for information that’s too processed is expressed in Eq. (8)
$${C}_{i}=Blowfis{h}_{SyK}({P}_{i})$$
(8)
$${P}_{i}=Blowfis{h}_{SyK}-1({C}_{i})$$
(9)
-
(v)
The ultimate output is to be processed by getting the concatenation of all decrypted blocks to get well information from the Android ransomware encrypted information as output expressed as P Plaintext in Eq. (10)
$$P = P_{1} left| {left| {P_{2} } proper|} proper|..||P_{n}$$
(10)
The primary focus of this analysis is to reinforce the deep studying mannequin with the SSO algorithm to optimize the numerous sample of the Android malware, whether or not it’s weak or regular information, with improved classification accuracy and highly effective characteristic extraction utilizing saliency. AlexNet for higher generalization over conventional deep studying fashions Lastly, hybrid cryptography makes use of excessive safety on Android units through the use of smaller key sizes and blowfish integration, making it a quick cryptographic mannequin to realize integrity and decrease computational overhead in a cloud atmosphere the place all info is saved34.