
Howdy 2025…and goodbye 2024! It’s been an thrilling first 12 months internet hosting the Security Bite column on 9to5Mac. I had the privilege of speaking with many leaders within the safety trade and touring to locations I by no means thought I’d discover myself. In October, I took to the column on the highway–sky and tracks, too–touring to Kyiv to satisfy with world-class safety engineers and to attend Objective-See‘s Goal for the We v2.0 occasion. It was an expertise I’ve but been capable of put into phrases—perhaps a narrative for one more day.
I digress. On this closing version of Safety Chunk for fiscal 2024, I up to date a narrative that I began engaged on in Might of final 12 months. As a result of Apple is constantly updating its XProtect suite to fight the most recent malware traits, this piece will proceed evolving.
Ever marvel what malware macOS can detect and take away with out assist from third-party software program? Apple constantly provides new malware detection guidelines to Mac’s built-in XProtect suite. Whereas most rule names (signatures) are obfuscated, with a little bit of reversing engineering, safety researchers can map them to their widespread trade names. See under what malware your Mac can take away!
9to5Mac Safety Chunk is completely delivered to you by Mosyle, the only Apple Unified Platform. Making Apple gadgets work-ready and enterprise-safe is all we do. Our distinctive built-in method to administration and safety combines state-of-the-art Apple-specific safety options for absolutely automated Hardening & Compliance, Subsequent Era EDR, AI-powered Zero Belief, and unique Privilege Administration with probably the most highly effective and trendy Apple MDM in the marketplace. The result’s a very automated Apple Unified Platform at the moment trusted by over 45,000 organizations to make thousands and thousands of Apple gadgets work-ready with no effort and at an inexpensive price. Request your EXTENDED TRIAL in the present day and perceive why Mosyle is every little thing you must work with Apple.
About Safety Chunk: Safety Chunk is a weekly security-focused column on 9to5Mac. Each week, Arin Waichulis delivers insights on information privateness, uncovers vulnerabilities, and sheds mild on rising threats inside Apple’s huge ecosystem of over 2 billion energetic machines. Keep safe, keep protected.

XProtect, Yara guidelines, huh?
XProtect was launched in 2009 as a part of macOS X 10.6 Snow Leopard. Initially, it was launched to detect and alert customers if malware was found in an putting in file. Nonetheless, XProtect has lately advanced considerably. The retirement of the long-standing Malware Removing Instrument (MRT) in April 2022 prompted the emergence of XProtectRemediator (XPR), a extra succesful native anti-malware part liable for detecting and remedying threats on Mac.
The XProtect suite makes use of Yara signature-based detection to determine malware. Yara itself is a extensively adopted open-source device that identifies information (together with malware) primarily based on particular traits and patterns within the code or metadata. What’s so nice about Yara guidelines is any group or particular person can create and make the most of their very own, together with Apple.
As of macOS 15 Sequoia, the XProtect suite consists of three principal parts:
- The XProtect app can detect malware utilizing Yara guidelines at any time when an app first launches, adjustments, or updates its signatures.
- XProtectRemediator (XPR) is extra proactive and may detect and take away malware by common scanning with Yara guidelines, amongst different issues. These happen within the background in periods of low exercise and have minimal impression on the CPU.
- The newest model of macOS contains XProtectBehaviorService (XBS), which displays system conduct in relation to crucial sources.
Sadly, Apple largely makes use of generic inner naming schemes in XProtect that obfuscate the widespread malware names. Whereas that is performed for good motive, it makes it difficult for these curious to know precisely what malware XProtect can determine.
For instance, some Yara guidelines are given extra apparent names, corresponding to XProtect_MACOS_PIRRIT_GEN, a signature for detecting the Pirrit adware. Nonetheless, in XProtect, you’ll largely discover extra generic guidelines like XProtect_MACOS_2fc5997 and inner signatures that solely Apple engineers would know, like XProtect_snowdrift. That is the place safety researchers like Phil Stokes and Alden are available.
Phil Stokes with Sentinel One Labs manages a helpful repository on GitHub that maps these obfuscated signatures utilized by Apple to extra widespread names utilized by distributors and located in public malware scanners like VirusTotal. Furthermore, Alden has lately made significant advancements in understanding how XPR works by extracting Yara guidelines from its scanning module binaries.
How do I discover XProtect on my Mac?
XProtect is enabled by default in each model of macOS. It additionally runs on the system stage, fully within the background, so no intervention is required. Updates to XProtect additionally occur robotically. Right here’s the place it’s situated:
- In Macintosh HD, go to Library > Apple > System > Library > CoreServices
- From right here, you’ll find remediators by right-clicking on XProtect
- Then click on Present Package deal Contents
- Broaden Contents
- Open MacOS
Observe: Customers shouldn’t rely totally on Apple’s XProtect suite, because it’s made to detect identified threats. Extra superior or refined assaults might simply circumvent detection. I extremely advise the usage of third-party malware detection and elimination instruments.
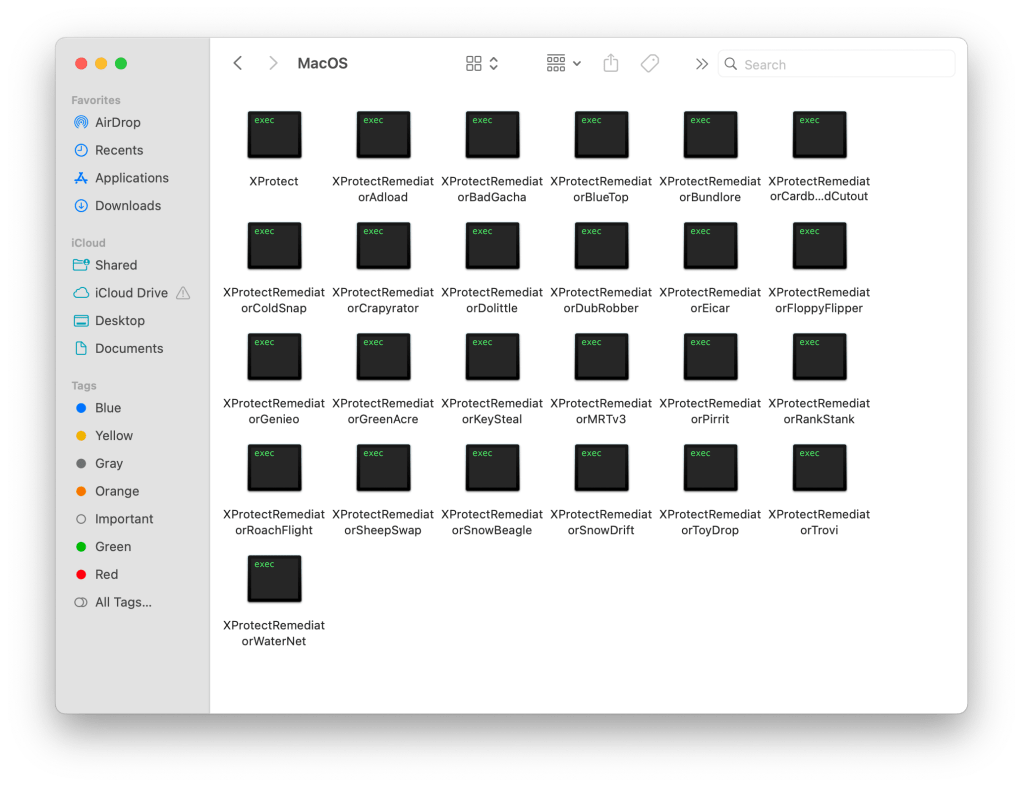
What malware can it take away?
Whereas the XProtect app itself can solely detect and block threats, it comes all the way down to XPR’s scanning modules for elimination. Presently, we are able to determine 14 of the 24 remediators within the present model of XPR (v147) to maintain malware off your machine.
- Adload: Adware and bundleware loader focusing on macOS customers since 2017. Adload was able to avoiding detection earlier than final month’s major update to XProtect that added 74 new Yara detection guidelines all aimed on the malware.
- BadGacha: Not recognized but.
- BlueTop: “BlueTop seems to be the Trojan-Proxy marketing campaign that was coated by Kaspersky in late 2023,” says Alden.
- CardboardCutout: Not recognized but.
- ColdSnap: “ColdSnap is probably going searching for the macOS model of the SimpleTea malware. This was additionally related to the 3CX breach and shares traits with each the Linux and Home windows variants.” SimpleTea (SimplexTea on Linux) is a Distant Entry Trojan (RAT) believed to have originated from the DPRK.
- Crapyrator: Crapyrator has been recognized as macOS.Bkdr.Activator. It is a malware marketing campaign uncovered in February 2024 that “infects macOS customers on a large scale, probably for the aim of making a macOS botnet or delivering different malware at scale,” states Phil Stokes for Sentinel One.
- DubRobber: A troubling and versatile Trojan dropper also referred to as XCSSET.
- Eicar: A harmless file that’s deliberately designed to set off antivirus scanners with out being dangerous.
- FloppyFlipper: Not recognized but.
- Genieo: A really generally documented probably undesirable program (PUP). A lot in order that it even has its personal Wikipedia web page.
- GreenAcre: Not recognized but.
- KeySteal: KeySteal is a macOS infostealer initially noticed in 2021 and added to XProtect in February 2023.
- MRTv3: It is a assortment of malware detection and elimination parts grandfathered into XProtect from its predecessor, the Malware Removing Instrument (MRT).
- Pirrit: Pirrit is a macOS Adware that first surfaced in 2016. It’s identified to inject pop-up adverts into net pages, gather personal person browser information, and even manipulate search rating to redirect customers to malicious pages.
- RankStank: “This rule is likely one of the extra apparent, because it contains the paths to the malicious executables discovered within the 3CX incident,” says Alden. 3CX was a provide chain assault attributed to the Lazarus Group.
- RedPine: With decrease confidence, Alden states RedPine is probably going in response to TriangleDB from Operation Triangulation.
- RoachFlight: Not recognized but.
- SheepSwap: Not recognized but.
- ShowBeagle: Not recognized but.
- SnowDrift: Recognized as CloudMensis macOS adware.
- ToyDrop: Not recognized but.
- Trovi: Much like Pirrit, Trovi is one other cross-platform browser hijacker. It’s identified to redirect search outcomes, monitor shopping historical past, and inject its personal adverts into search.
- WaterNet: Not recognized but.
Thanks all for studying! I’m excited to proceed security-specific my protection right here on 9to5Mac via 2025! Cheers.
Extra in Apple safety
Follow Arin: Twitter/X, LinkedIn, Threads
FTC: We use revenue incomes auto affiliate hyperlinks. More.






