.jpg)
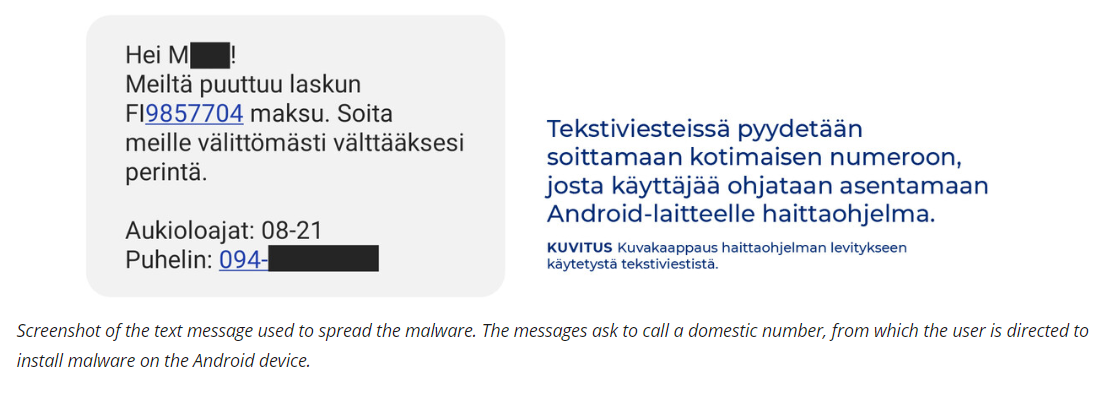
Security experts have recently unearthed a highly sophisticated Android banking trojan, dubbed “Brokewell,” that boasts the capability to capture an array of device interactions, from user inputs such as taps and text to the launching of applications. This malware finds its way onto devices through a deceptive lure, posing as an update for Google Chrome, presented to users while navigating the web browser. Alarmingly, Brokewell is currently in an active development phase and is designed with a potent combination of device takeover and remote manipulation features, marking a significant threat to Android users.
The investigative team at ThreatFabric stumbled upon Brokewell while analyzing a seemingly innocuous Chrome update page which, in reality, served as a conduit for deploying the malware. This method, designed to prey on unsuspecting users, is a classic tactic in the cybercriminal playbook. Historical scrutiny of past campaigns revealed that Brokewell had previously targeted financial services offering “buy now, pay later” options, such as Klarna, and masqueraded as the Austrian digital authentication app, ID Austria, showcasing its versatility in deception.
Brokewell’s arsenal is alarmingly comprehensive, with functionalities that extend far beyond simple data theft. The trojan is engineered to mimic the login interfaces of targeted apps to harvest credentials via overlay attacks and employ its own WebView to intercept and siphon off cookies post-authentication on legitimate sites. It meticulously records every interaction made by the victim on the device, capturing sensitive data entered or displayed. The malware is also equipped to gather detailed information about the device’s hardware and software configurations, access call logs, pinpoint the device’s physical location, and even covertly record audio using the device’s microphone.
Further deepening concerns, Brokewell possesses an extensive array of device control capabilities. It enables attackers to view the device’s screen in real-time, execute touch and swipe gestures remotely, and perform actions as if they were physically handling the device. This includes simulating button presses and remotely activating the device’s screen to augment the potential for data capture. Additionally, settings manipulation, such as dimming screen brightness or lowering volume to stealthily operate without the user’s awareness, is within its capabilities.
In a concerning twist, the brains behind Brokewell is identified as an individual known as Baron Samedit, a figure previously linked to the sales of tools for scrutinizing stolen accounts. Alongside Brokewell, ThreatFabric uncovered another tool — the “Brokewell Android Loader,” also the brainchild of Samedit. This tool is especially noteworthy for its ability to skirt around security restrictions introduced in Android 13 and later versions, aimed at curtailing the misuse of Accessibility Services by side-loaded apps (APKs).
Samedit’s loader highlights a pervasive issue, with techniques to bypass such restrictions gaining traction among cybercriminal circles since mid-2022. The scenario grew more grim towards the tail end of 2023, marking a concerning evolution in the sophistication and availability of malware deployment mechanisms that abuse these security loopholes.
Security experts are sounding the alarm over Brokewell’s advanced device takeover functionalities, which are highly sought after in the cybercriminal community. Such capabilities facilitate the execution of fraudulent activities directly from the victim’s device, cleverly evading detection by fraud prevention tools. The expectation is that Brokewell will continue to evolve and make its way to underground forums, eventually being marketed as a malware-as-a-service (MaaS) to other nefarious actors.
In light of the rising tide of Android-based malware threats, experts underscore the importance of adhering to secure practices. Users are urged to refrain from downloading apps or updates from sources outside of the official Google Play Store and to ensure that Google’s Play Protect feature is perpetually enabled, providing a critical layer of defense against such invasive and malicious software.
Source