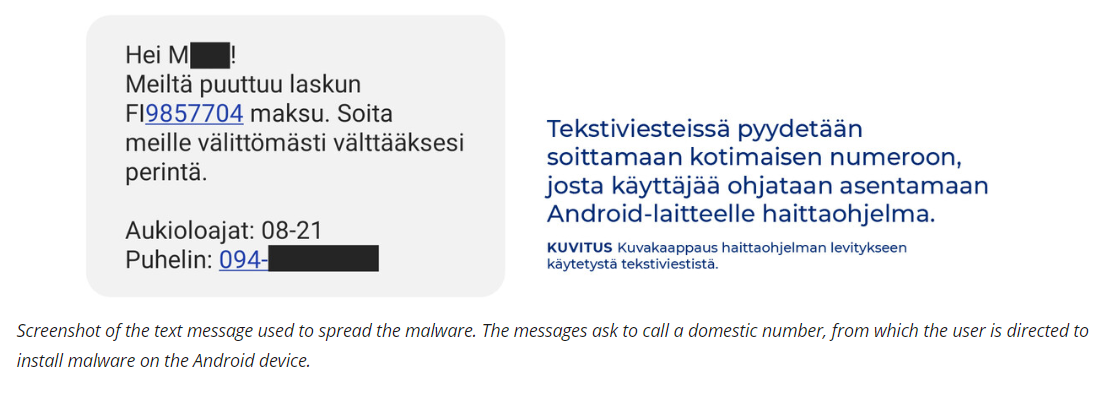
In a recent revelation by BleepingComputer, the cybersecurity community has been put on high alert with the discovery of a new malware strain targeting Android devices. Dubbed ‘Brokewell’, this banking trojan has raised concerns over its sophisticated capabilities to compromise user data and potentially take full control of the infected devices.
The initial mode of infection traced back by cybersecurity experts involves a deceptive strategy where users are lured into downloading what is presented as a Google Chrome update from fraudulent web pages. However, clicking on these links initiates the installation of the Brokewell trojan instead of any legitimate software update. According to a detailed report by ThreatFabric, this marks the starting point where users’ data becomes vulnerable to theft and unauthorized access.
Brokewell is particularly alarming due to its wide array of techniques for exfiltrating sensitive information. The malware showcases an ability to mimic login screens of targeted applications, compelling users to inadvertently hand over their credentials. Beyond this, it employs WebView to siphon off website cookies, thus gaining further access to users’ online activities and accounts.
But the intrusion doesn’t end with stealing login details and cookies. Brokewell extends its reach into capturing text inputs and tracking user interactions across the device. This includes recording call logs, collecting information about the device’s hardware and software configurations, and even capturing audio data. These capabilities signify the high level of surveillance that attackers can achieve, painting a grim picture of privacy infringement for victims.
More troublingly, the malware grants attackers the power to control the infected device remotely. Functions such as real-time screen streaming, executing gestures, remotely performing screen clicks and scrolls, and even adjusting the device’s brightness and volume levels are within the realm of possibilities for those wielding Brokewell. Such features not only pave the way for further data compromise but also potentially allow for more intrusive forms of cyberattacks.
The origins of Brokewell trace back to an individual known as Baron Samedit, a figure who has been active in the cyberspace underworld, trading various hacking tools over the last couple of years. Researchers from ThreatFabric hint at the possibility that Brokewell could soon evolve into a malware-as-a-service (MaaS) operation, widening its distribution channels and possibly enhancing its malicious functionalities.
As the Android user community navigates this threat, the emergence of Brokewell serves as a stark reminder of the ever-present and evolving risks in the digital world. Cybersecurity firms and researchers continue to monitor the situation closely, seeking ways to mitigate the impact of this potent banking trojan and safeguard users against its destructive capabilities.
Source