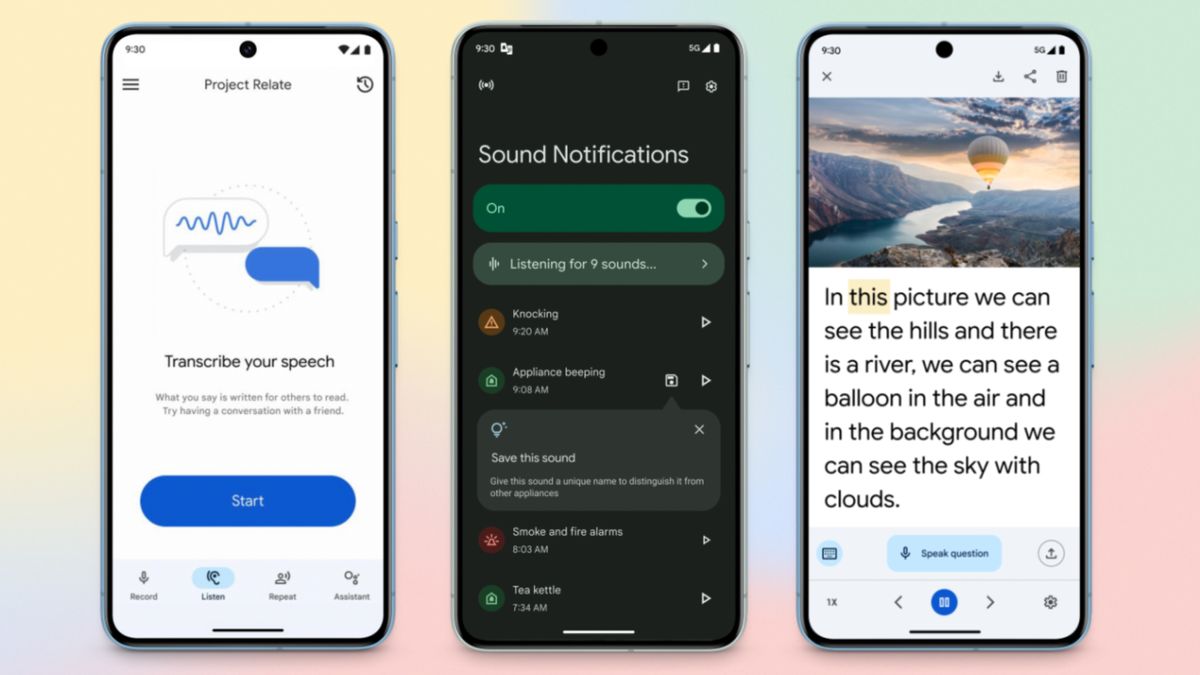
Upgrade Alert: Passkeys now available on Wear OS 5 with Gboard on Android 15!
Passkeys: Google's Effort Toward Easier Sign-Ins At I/O 2024, Google’s work on passkeys continues with an even easier sign-in process, as ...
Mustafa Suleyman Praises Microsoft: ‘A Leading Force in AI Innovation!’

Angle down icon An icon in the shape of an angle pointing down. Mustafa Suleyman, previously a founder of Google's DeepMind AI lab, posted on social media about why his first month at ...
Apple Unfolds the Future: Hybrid Mac/iPad in 2025, Foldable iPhone by 2026
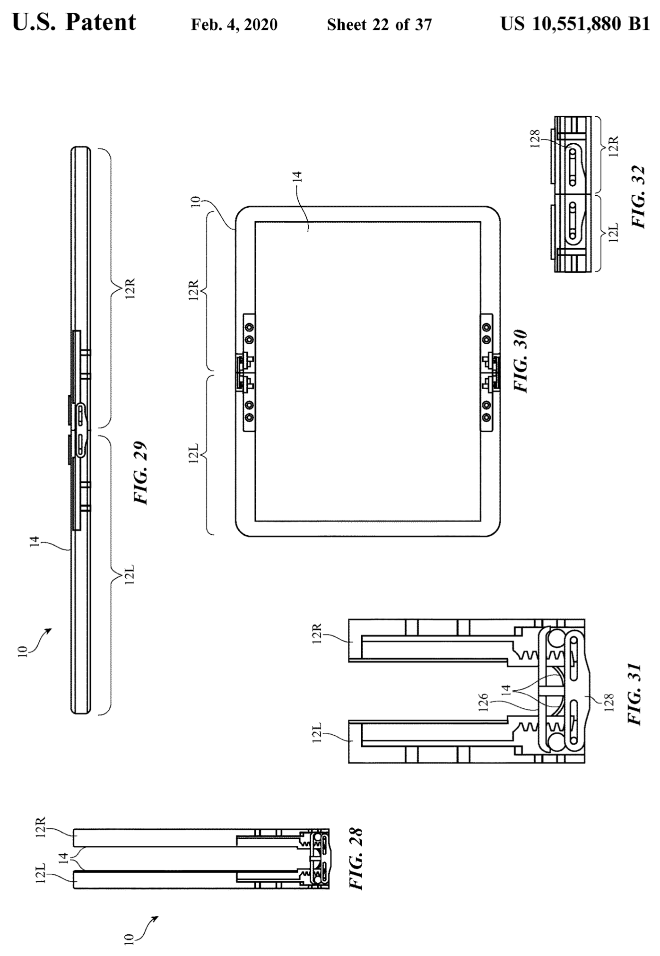
In a noteworthy development within the tech industry, Haitong International Securities analyst Jeff Pu has provided insights into Apple's plans concerning future foldable devices. According to Pu, ...
Intel Boosts Quantum Leap: Eyes on Qubit Yield & Uniformity in R&D Drive

In the evolving landscape of quantum computing, the crucial yet often overlooked metric of device yield is coming to the fore, especially as the industry gears towards making quantum processors more ...
Get Wood for Gaming: The CORSAIR ONE i500 Brings Compact Power with Windows 11!
In an exciting announcement for tech enthusiasts, CORSAIR has unveiled the ONE i500, a cutting-edge compact PC that promises to bridge the gap between high performance and sleek design. Aimed at ...
Nintendo Stands Firm on Game’s No-Gay Policy Amidst Backlash

In a move that has sparked considerable backlash on social media, Nintendo Co Ltd (7974.T) stands firm on its decision to prohibit same-sex relationships in the popular mobile game, "Tomodachi Life." ...
Apple’s Folding Future: Surprising Device to Debut Bendable Screen, Not iPhone or iPad!
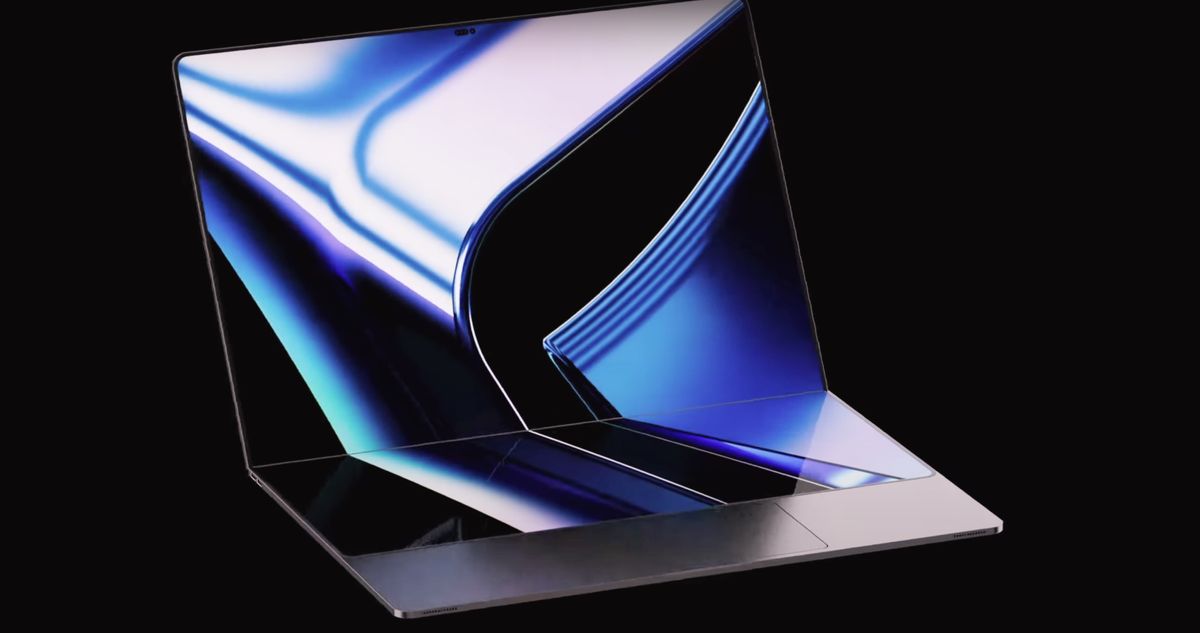
In a move that could mark a significant pivot in laptop design, Apple has recently unveiled its latest MacBook Air models, an announcement that, while leaving little to the imagination in terms of ...